After Cryptopia Hack, 2,000 Wallets Still Might be at Risk (UPDATED)
Following the first reported hack in 2019, on New Zealand cryptocurrency exchange Cryptopia, there is a significant lack of information publicly available about the aftermath. Currently, around 2,000 wallets remain on the exchange with a total of around 380 ETH, which is around USD 46,000, and they still might be at risk, according to Max Galka, co-founder and CEO of Elementus, a blockchain analysis protocol and platform. (A new section (Inadequate security) has been added to the article.)

Most of the funds that potentially remain at risk have been deposited after the security breach occurred, presumably by users who had not heard about the hack, Galka explained in a blog post. If the thieves have access to these wallets, they may very well be lost – but if Cryptopia still has access to them, they have hopefully already contacted the owners, or people will lose that money as well, he wrote, adding that it’s likely that the exchange has additional funds safely stashed away somewhere.
Cryptopia did not respond to our request for comment.
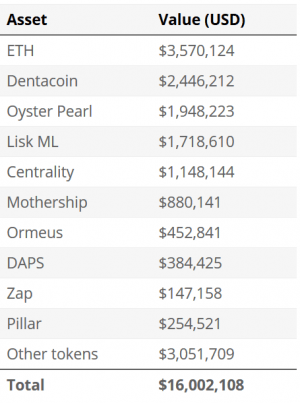
“By our calculations, the total value of the stolen crypto (ether and various tokens), at current market prices, comes out to about USD 16 million. This number includes only what’s on the Ethereum blockchain (ether and ERC20 tokens). We have not examined the Bitcoin blockchain or other blockchains to see if funds were stolen there as well,” according to Galka.
The breakdown of potential losses:
Meanwhile, other researchers claim that BTC 606 might have been stolen from Cryptopia:
For the last few days, the hackers have been shuffling the funds around in small pieces and gradually moving them into exchanges in order to cash out, according to Galka.
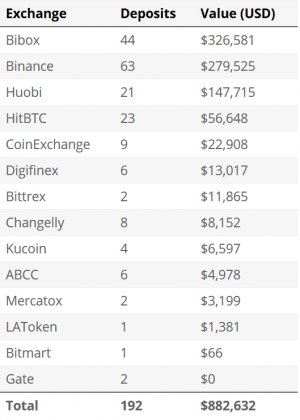
As previously reported, Binance has frozen some of the funds that have been stolen from Cryptopia.
According to Elementus, Cryptopia has not been very quick on the uptake even when the initial breach happened. Not only did the hackers take their time siphoning out the funds – over a course of almost five days – but Cryptopia seemed powerless to stop them, even though they should not have had these issues. A plausible explanation is that the exchange simply lost access to the wallets – a total of 76,000.
According to Galka, around USD 15m are in two wallets controlled by the thieves:
0x9007a0421145b06a0345d55a8c0f0327f62a2224
0xaa923cd02364bb8a4c3d6f894178d2e12231655c
The breach was initially announced at 8 am UTC on January 15th. The exchange added that they would “remain in maintenance mode, with trading suspended” until the matter is investigated. The irregularities had first been brought to light when the exchange experienced an “unscheduled maintenance” just thirteen hours earlier, likely a preemptive hint that it had fallen victim to a hack. The exact specifics of the cryptocurrencies lost weren’t plainly stated. Prior the hack announcement, the 24-hour trading volume on the exchange was almost USD 1 million, according to coinmarketcap.com data.
Inadequate security
What is clearer from the attack is that cybersecurity at some exchanges is woefully inadequate, with Elementus stating that the most likely explanation for Cryptopia’s failure to do anything about the hack is that it had their customers’ private keys “stored in a single server with no redundancy.”
In other words, because Cryptopia had private keys stored on a single server, the hackers would have been able to wipe these keys from this server after stealing funds, something which would have prevented the exchange from doing anything to access its wallets.
And while Elementus isn’t in a position to comment directly on Cryptopia’s possible reasons for maintaining only a single server, its Chief Product Officer, Mike Kalomeni, tells Cryptonews.com that there are no legally enforced security standards for crypto-exchanges. So it is perhaps only a matter of time before something like this happens (and happens again).
“A single server is the easiest to maintain, and the operating costs are the lowest,” he says. “We don’t have any answers on the cybersecurity side of the hack. Most importantly, there are no standards on how exchanges should maintain private keys of accounts. Everyone needs to come up with their own solution. Cryptopia has been around for a long time but, so far, there is no [publicly agreed] right way to do it.”
Similarly, Kalomeni points out that the lack of sufficient know-your-customer (KYC) measures at some exchanges, as well as the lack of standardized tracking systems, may have made it easier for the hackers to siphon their ill-gotten funds to 14 other exchanges.
“By spreading the amount stolen, as a hacker, you average out the risks of having the accounts frozen,” he explains. “Adding the lack of KYC and the risks become fairly low. When we look at cybercrime activities, we observed that indeed multiple exchanges are used to launder the same dirty money (same origin). The exchanges may have different transactions’ monitoring systems among each other, and not necessarily good enough.”
This all paints a grim picture of the security at some of the smaller exchanges, which is perhaps not helped by how, according to Kalomenia, Cryptopia refused to reply to Elementus regarding its findings. Still, Elementus nonetheless tells us that at least some of the exchanges to which funds had been laundered were disturbed to learn that they’re now indirectly involved in the hack.
“The most professional exchanges were very concerned to find the dirty money coming to their accounts, and were eager to find a solution to set a standard of transactions’ monitoring. Others didn’t seem too concerned about regulatory risks.”



