Quantum Computers May Break Bitcoin by 2030, But We Won’t Know About It

Quantum computers might sound like another buzzword in the tech world, yet their threat to cryptocurrency is very real and approaching fast. Scientists may differ on the timeline, but they all agree: “Q-day” is not a matter of if, but when.
We’ve spoken to quantum experts around the world to hear the latest estimates on when it will happen, what can be done to protect cryptocurrency, and whether these powerful machines could somehow benefit the crypto world.
Key takeaways:
- Quantum computing might soon break cryptocurrency security. Experts predict potential breaches by 2030. Despite differing timelines, all agree quantum technology will eventually impact cryptocurrencies.
- Implementing post-quantum cryptography and updating blockchain protocols are essential to protecting crypto assets, but it is not easy to do.
- Early adopters of quantum-resistant technologies may gain market advantages, attracting investors to “quantum-safe” cryptocurrencies.
- The rise of quantum computing could lead to stricter regulations, protecting investors from vulnerable cryptocurrencies.
- Quantum computing may offer unexpected advantages to the crypto industry.
What Is Quantum Computing?
Unlike traditional computers, which use bits as the smallest unit of data, each bit being a 1 or a 0, quantum computers use quantum bits, or qubits. These qubits can exist in 0 and 1 states or in multiple states at once—a property called superposition.
This allows quantum computers to perform calculations simultaneously and process large amounts of data much faster than standard computers.
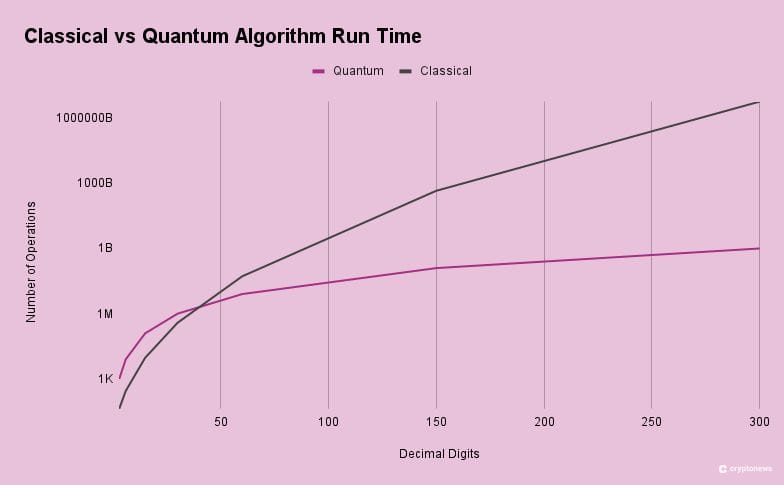
As quantum computers can hold and process many possible outcomes at once, it reduces the time needed to solve problems that depend on trying many different solutions, such as factoring large numbers, which is the foundation of most cryptocurrency encryption.
Factoring large numbers, or integer factorization, is a mathematical process of breaking down a large number into smaller, simpler numbers called factors, which, when multiplied together, result in the original number. The process is called prime factorization if these integers are further restricted to prime numbers.
How Quantum Computers Can Threaten Cryptocurrency
In cryptocurrency, security heavily relies on the mathematical relationship between private and public keys. A public key is a long string of characters associated with the wallet address. It can be shared openly. A private key, used to sign transactions, must remain confidential. This mathematical relationship is one-way, meaning that a public key can be derived from the private key but not the other way around.
Itan Barmes, who is the Global quantum cyber readiness capability lead at Deloitte, explained in a conversation with Cryptonews:
“The quantum computer breaks this one-way relationship between the two. So, if you have someone’s public key, you can calculate their private key, impersonate them, transfer their funds elsewhere.”
The task is currently nearly impossible for conventional computers. However, in 1999, mathematician Peter Shor showed that a quantum computer could solve the factoring problem much faster. Shor’s algorithm can also solve the Discrete Logarithm Problem, which is the basis for the security of most blockchains. This means if such a powerful quantum computer existed, it could break the cryptocurrency security model.
Not all cryptocurrencies would face the same level of risk from quantum attacks. In 2020, Itan Barmes and a team of Deloitte researchers examined the entire Bitcoin blockchain to determine how many coins were vulnerable. They discovered that about 25% of Bitcoins could be at risk.
|
“Pay To Public Key” |
“Pay to Pubkey Hash” |
|
These addresses directly use the public key, making them visible and vulnerable to quantum attacks. |
These addresses use a cryptographic hash of the public key. They don’t expose the public key directly until coins are moved. |
Vulnerable coins include those held in P2PK (“Pay To Public Key”) addresses, which directly expose the public key, making them easy targets for a quantum attack. Coins in reused P2PKH (“Pay to Pubkey Hash”) addresses are also at risk because these addresses display their public key when the owner moves the funds. This attack is called the storage attack, as it applies to coins residing in static addresses. Itan Barmes further explained:
“A quantum attack only applies to specific coins, not everything. If we conducted the same research today, the percentage of vulnerable coins would be lower because the number of vulnerable addresses remains more or less the same, but due to mining, there are more coins in circulation.”
Itan Barmes added that in addition to the storage attack, there is also an attack on active transactions, as the public key is exposed for the first time.
“Such an attack must be performed within the mining time (for Bitcoin, around 10 minutes), which adds a requirement for the quantum computer to not only be powerful enough but also fast. This so-called ‘transit attack’ is likely to be possible later than the storage attack due to this additional requirement.”
Ideally, Bitcoin users must generate a new address for each transaction. Yet, recent research by Bitmex suggests that about 50% of transaction outputs still go to previously used addresses, which means the practice of address reuse is more common in Bitcoin transactions than we may think.
Will Bitcoin Be Cracked by 2030?
Are we nearing the point where quantum computers can pose a real threat? In 2017, a group of researchers, including Divesh Aggarwal and Gavin Brennen, published an article warning that the elliptic curve signature scheme used by Bitcoin “could be completely broken by a quantum computer as early as 2027, by the most optimistic estimates.”
Cryptonews reached out to the authors to ask whether their estimation has shifted. Gavin Brennen from Macquarie University in Australia replied that although a lot has changed in quantum computing space since then, the basic message is still the same:
“Quantum computers pose a threat to blockchains, primarily by attacks on digital signatures, and cryptocurrencies should get started sooner rather than later to upgrade their systems to use post-quantum cryptography before their asset valuations are threatened.”
To be able to break cryptocurrency security, quantum computers will likely need thousands, if not millions, of qubits. Currently, the most advanced machines have around 1000.
Another critical challenge is error reduction. Quantum bits are highly sensitive to their environment; even the slightest disturbance, like a change in temperature or vibration, can cause errors in computations, a problem known as quantum decoherence.
Dozens of companies, both public and private, are now actively advancing the development of large quantum computers. IBM has ambitious plans to build a 100,000-qubit chipset and 100 million gates by the end of this decade.
PsiQuantum aims to achieve 1 million photonic qubits within the same timeframe. Quantum gate fidelities and quantum error correction have also significantly advanced. Gavin Brennen continued:
“What all this means is that estimates on the size of quantum computers needed to crack the 256-bit elliptic curve digital signatures used in Bitcoin have dropped from 10-20 million qubits to around a million. One article published by the French quantum startup Alice & Bob estimates that it could be cracked with 126,000 physical qubits, though that does assume a highly specialized error model for the quantum computer. In my opinion, a plausible timeline for cracking 256-bit digital signatures is by the mid-2030s.”
Gavin Brennen added that substantial technological improvements would be required to reduce all types of gate errors, connect modules, and combine fast classical and quantum control, which is “a challenging but surmountable problem.”
Yet, if quantum technology becomes powerful enough to break cryptocurrency security, we may not even know about it, believes Marcos Allende, a quantum physicist and CTO of the LACChain Global Alliance. In an email conversation with Cryptonews, Allende wrote:
“What is certain is that those who reach that power first will use it silently, making it impossible to guess that selected hackings are happening because of having quantum computers.”
“Quantum Computers Are All Terrible”
Many scientists remain skeptical about the quantum threat to cryptocurrency. Winfried Hensinger, a physicist at the University of Sussex in Brighton, UK, speaking to Nature magazine, described quantum computers as “They’re all terrible. They can’t do anything useful.”
Several challenges keep quantum computing from reaching its full potential. The delicate nature of qubits makes it difficult to maintain them in a quantum state for extended periods. Another challenge is cooling requirements. Many quantum processors must operate at temperatures close to absolute zero, which means they need complicated and costly refrigeration technology. Finally, the quantum systems would need to be integrated with the existing classical ones.
“Just having 200 million qubits not connected to each other is not going to do anything. There are a lot of fundamental physics problems that need to be resolved before we get there. We are still very much at the beginning. But even in the past year, there’s been tremendous improvement. The technology can accelerate in a way that all the timelines will be much shorter than we expect,” Itan Barmes told Cryptonews.
Crypto Industry Needs a Plan
Tommie van der Bosch, Partner at Deloitte and Blockchain & Digital Asset Leader of Deloitte North and South Europe, believes that the question is not if quantum computing will break cryptocurrency security but when: “The fact that it’s a possibility is enough to start taking action. You should have a plan.”
Indeed, this year several key crypto companies and the World Economic Forum (WEF) have shared concerns about the implications of quantum computing on cryptocurrency security.
The WEF, in its post published in May, warned that central bank digital currency (CBDC) could become a prime target for quantum attacks. Ripple’s recent report has also said that quantum computers could break the digital signatures that currently protect blockchain assets.
Earlier this year, Buterin, Ethereum founder, suggested the Ethereum blockchain would need to undergo a “recovery fork” to avoid the scenario when “bad actors already have access to them and are able to use them to steal users’ funds.”
To protect against these potential quantum attacks, blockchain systems will need to integrate post-quantum cryptographic algorithms. However, incorporating them into existing blockchain protocols is not easy.
New cryptographic methods must first be developed, tested, and standardized. This process can take years and requires the consensus of the cryptographic community to ensure the new methods are secure and efficient.
In 2016, the National Institute of Standards and Technology (NIST) started a project to set new standards for post-quantum cryptography. The project aims to finalize these standards later this year. In 2022, three digital signature methods—CRYSTALS-Dilithium, FALCON, and SPHINCS+—were chosen for standardization.

Once standardized, these new cryptographic algorithms need to be implemented within the blockchain’s existing framework. After that, all network participants need to adopt the updated protocol.
Itan Barmes explained, “Let’s say someone could tell us exactly the date, three years from now, when we will have these kinds of quantum computers. How quickly do you think we can change the Bitcoin protocol to make it resilient to these attacks? The decentralized governance of Bitcoin can turn out to be a double-edged sword, by preventing timely action.”
Quantum-resistant algorithms often require more processing power and larger key sizes, which could lead to performance issues on the blockchain. These include slower transaction times and increased computational requirements for mining and verification processes.
Shifts in Economic Model and Regulation
Tommie van der Bosch told Cryptonews that, ultimately, the rise of quantum computing could affect the entire economic model of cryptocurrencies.
Coins that upgrade to quantum-resistant protocols in time might gain a competitive advantage. Investors and users could prefer these “quantum-safe” cryptocurrencies, as they may see them as more secure long-term holdings. This shift could lead to an increase in demand for such cryptocurrencies, potentially enhancing their value and market share compared to those that are slower to adapt. Tommie van der Bosch told Cryptonews:
“Let’s draw a parallel with the banking system. We’ve all seen the effects of a bank collapsing or even the rumor of one. Your money suddenly seems at risk. How quickly do people shift their assets? It can trigger a domino effect.”
The development of quantum computing could also bring regulatory changes. Regulators could start enforcing stricter standards around trading and custody of cryptocurrencies that haven’t updated their cryptographic protocols. Such measures would aim to protect investors from sinking funds into potentially vulnerable assets.
Itan Barmes remarked, “Not many people are aware that the cryptographic algorithm used in Bitcoin and essentially all cryptocurrencies is not part of the NIST recommendation (NIST SP800-186). The issue is already present if organizations require compliance to NIST standards. The issue becomes even more complex if algorithms need to be replaced; Who’s responsibility is it to replace them?”
Could Quantum Computers Be Good for Cryptocurrency?
Could quantum computing actually benefit the cryptocurrency industry? Gavin Brennen suggests it might. In an email exchange with Cryptonews, Brennen discussed the development of quantum-enabled blockchains.
Quantum computers could accelerate mining, although Brennen notes that the improvement over traditional mining rigs would be limited and require quantum computers with hundreds of millions of qubits—far beyond current capabilities.
“New computational problems have been suggested, like the boson sampling problem, that are slow for all types of classical computers but would be fast on a quantum device. Interestingly, the boson sampler is a small, specialized processor using photons of light, that is not as powerful as a full quantum computer, but much cheaper to build, and that solves a problem immune to ASIC speedups with an energy footprint that is orders of magnitude lower for reaching PoW consensus.”
Currently, proof-of-work (PoW) requires vast amounts of electrical power for mining, raising concerns about sustainability and environmental impact. Boson sampling could become a greener alternative, significantly reducing the energy footprint of blockchain operations while maintaining security and efficiency.








