Cryptocurrency Security Guide – How to Stay Safe in Crypto
The world of crypto comes with a learning curve, much of which revolves around crypto security: how to keep your investment safe. In this guide, we’ll discuss the must-know aspects of crypto security, ranging from best practices for storage to ways to avoid scams and hackers.
We’ll also discuss how cryptocurrencies work under the hood. Understanding the basics goes a long way when it comes to improving your crypto safety. Let’s dive in.
What Is Crypto Security?
Cryptocurrency security is a broad topic surrounding strategies and best practices for safeguarding against threats and keeping your cryptocurrency investment safe. Risks range from dubious cryptocurrency exchanges to phishing scams, malicious smart contracts, and even man-in-the-middle attacks. While that all sounds terrifying, many of the same risks also apply to traditional finance.
Regardless of which assets you trade, someone else wants what you have. However, one primary difference compared to traditional finance is that crypto isn’t protected by any government programs like FDIC or SIPC insurance. These programs can protect against the insolvency of a custodian, like a bank or broker.
In the crypto world, you’re on your own to protect your investment. Following best practices can help you stay alert to risks and prevent unexpected losses while you explore the many opportunities crypto has to offer. In the following sections, we’ll explain how cryptocurrency works and then discuss tips to help you keep your crypto assets secure.
How Does Cryptography Enhance Security?
First, let’s discuss some cryptocurrency security basics. This will help when we discuss wallets in a bit. Cryptocurrency gets its name from the cryptography used to secure the digital assets on a blockchain.
For example, the Bitcoin network uses SHA-256 encryption for wallet addresses, wallet keys, transaction hashes, and the transactions within each block. A hash is an encrypted value. Let’s look at an example.
| Input | SHA-256 Output |
| This is a test. | a8a2f6ebe286697c527eb35a58b5539532e9b3ae3b64d4eb0a46fb657b41562c |
| This is a test! | 54ba1fdce5a89e0d3eee6e4c587497833bc38c3586ff02057dd6451fd2d6b640 |
The same input will always generate the same hash, but changing just one character results in a completely different hash value. Hashes are hexadecimal (letter and number) strings of a fixed length. However, while not all cryptocurrencies use the same hash algorithm, they all use hashes to secure the network and prevent fraudulent transactions. You can think of a hash as being like a fingerprint.
From a crypto security standpoint, the most important use of hashes and cryptography centers on crypto wallets. Crypto wallets use public-key cryptography, also known as asymmetric encryption, a time-tested message encryption method that dates back to the 1970s.
A crypto wallet generates and stores a private key (for your eyes only) and a public key, the latter of which is used for receiving transactions with publicly visible wallet addresses.
For example, the wallet address below was used for the first Bitcoin transaction, 50 mined bitcoins. This wallet address is known, but crypto wallet addresses allow you to transact without sharing your identity. Your wallet address becomes your pseudonymous identity on the blockchain network.
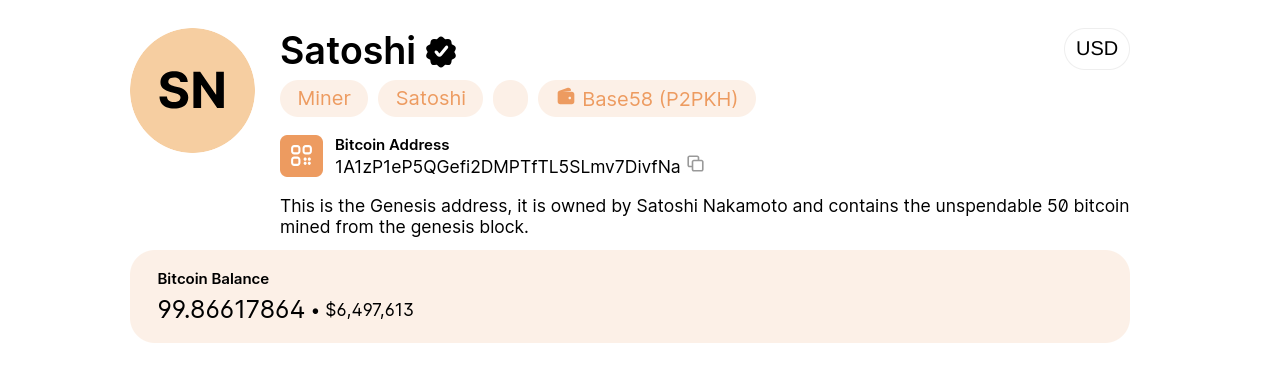
The private key is used for sending transactions. Anyone with the private key can control your crypto assets on the blockchain. Hence, the need for crypto security. Cryptography is at the heart of crypto transactions, but it’s essential to safeguard the private key that can unlock your crypto.
Security Tips for Using Crypto Exchanges
For many investors, the first stop on the crypto journey is a crypto exchange, where they can buy crypto with traditional fiat currencies like USD or GBP. Exchanges use crypto wallets controlled by the exchange to hold your crypto, but the account is usually secured with a password.
This means anyone who gets into your exchange account can send your crypto elsewhere. Furthermore, if you linked a payment method to the exchange, someone with access to your exchange account can also buy crypto with your funding source and then send the crypto to another wallet you can’t access.
That sounds risky. Let’s look at some ways to improve your crypto exchange security.
Use a Trustworthy Exchange
Crypto exchanges offer a convenient way to buy or sell crypto, and by some estimates, there are now more than 600 crypto exchanges worldwide. Not all of these exchanges are trustworthy, however, and some are downright dodgy.
In fact, some people would say none of them are are trustworthy. In a later section, we’ll discuss the best ways to move your crypto off the exchange. But when you’re buying and selling, you’ll want to choose an exchange that’s well-tested and takes security seriously.
Leading exchanges like Coinbase and Kraken use offline cold storage to hold crypto for customers. Kraken provides proof of reserves, a method of proving the exchange has the crypto showing on your account dashboard using blockchain technology. Coinbase is a publicly traded company with rigorous reporting requirements. Coinbase is also working on an on-chain verification method.
If you must transact on an exchange you’re not sure about, consider using a one-time use debit card, also called a privacy card. These card numbers can only be used once. In many cases, you can also deposit crypto for trading, which sidesteps the possibility of someone using a connected bank account.
Two-Factor Authentication
Many exchanges now require users to enable two-factor authentication (2FA). This strategy requires you to authorize a new login on a device in your possession. In other words, someone on the other side of the planet can’t log in — even if they have the password. Look for the setting to enable 2FA when using an exchange.
Use a Secure Password
We all know we shouldn’t use the same password for multiple sites, right? If someone hacks the local library’s online database and you use the same email address and password for your bank account or exchange account, the library hacker can also access the financial accounts. This type of login information is sold on the dark web in bulk.
Use unique and secure passwords with mixed-case letters, numbers, and special characters.
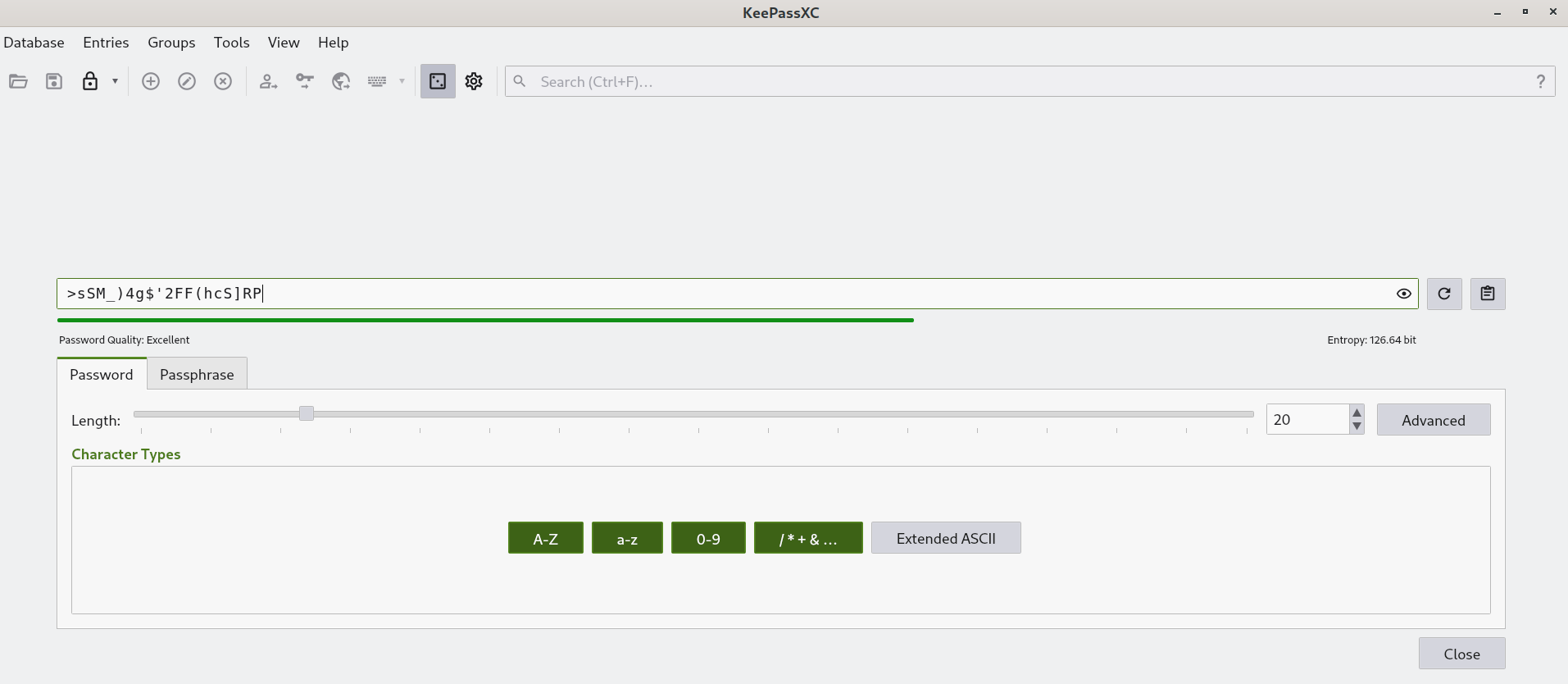
Cross-platform tools like Bitwarden and KeePassXC can help you generate and save secure passwords without relying on your browser to store them.
Watch Out For Phishing
Phishing refers to when someone tries to trick you into revealing your login details. This type of hacking attempt can arrive in your email inbox, via text messages, or even by phone. Phishing can also include fake websites or apps that look like real websites for crypto apps.
Scammers are becoming more clever in their phishing techniques. For example, one technique involves phone calls pretending to be from a cloud email provider’s ‘fraud department.’ In this case, the fraud moniker fits. The scammers are trying to get access to the email address to bypass two-factor authentication. Be careful out there, and remain vigilant. They want your crypto.
Move Your Crypto to a Self-Custody Wallet
We’ll get into this in more detail in a bit, but crypto security best practices include taking your crypto off the exchange if you’re not actively trading. If an exchange is hacked or becomes insolvent, your crypto won’t be part of the loss. To do this, you’ll need a self-custody crypto wallet.
Crypto Wallet Security Measures
Your crypto wallet holds the keys to your crypto kingdom. The wallet itself is empty, devoid of any crypto assets; the assets exist on the blockchain. What your wallet holds is the keys to control your assets on the blockchain. And that’s why crypto wallet security is so crucial.
Safeguarding Private Wallet Keys
A crypto wallet holds the private keys that control your crypto assets on the blockchain. To send crypto from your wallet address, you have to ‘sign’ the transaction with your wallet using the private key. Most wallets also use a seed phrase, which is usually a 12 to 24-word string of words. The seed phrase, sometimes called a recovery phrase, is a human-readable version of the private key.
Anyone with access to the private key or the wallet seed phrase can access your crypto assets. Both can be used to recreate the wallet remotely.
- Don’t share your private key.
- Don’t share your seed phrase.
Also, be careful on crypto discussion boards. One common scam is to masquerade as tech support for a project and then offer to ‘reset your wallet’ or something similar if you ask a question on the board.
The process, of course, requires sharing your seed phrase. This allows the scammers to recreate your wallet remotely and send the crypto elsewhere. Often, these scammers message users privately. After the heist, the scammers disappear.
Don’t fall for it. They want your crypto.
Use a Cold Wallet for Long-Term Storage
You can choose from hot wallets or cold wallets for crypto storage. A hot wallet generates and stores your private keys on a device connected to the internet. Typically, a hot wallet is a mobile app or browser extension.
Cold wallets, on the other hand, generate and store your private keys on a device that’s not connected to the internet. Often, these devices connect via USB or Bluetooth but do not have internet access. When you need to sign a transaction, you use the interface on the cold wallet.
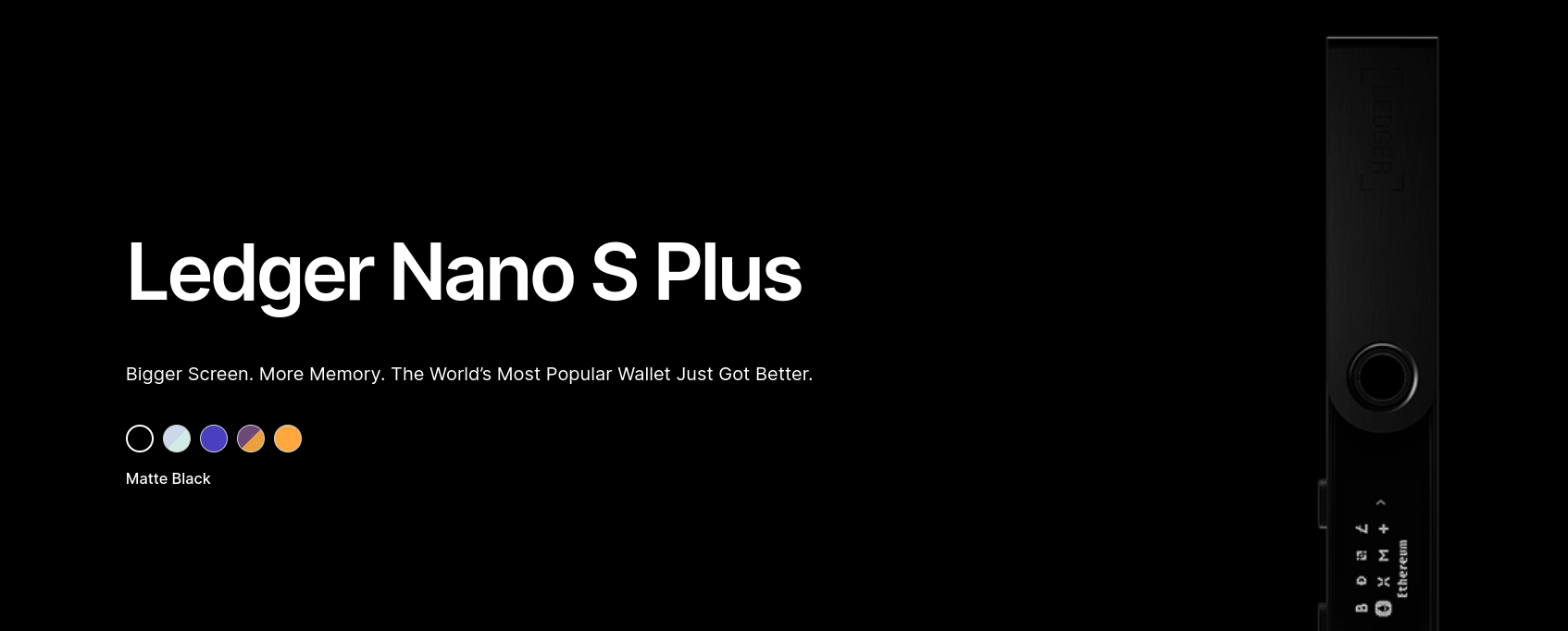
Also called hardware wallets, some cold wallets can also operate completely offline, using QR codes to communicate with an external app rather than connecting wirelessly or via USB.
Cold wallets are considered to be the safest storage for crypto and can improve your crypto security for larger balances or balances you don’t need immediately. Popular devices like the Ledger Nano S Plus start at under $80.
Double-Check Addresses
Unlike traditional finance, where you can dispute a charge, a crypto transaction can’t be reversed. If you send crypto to the incorrect wallet address by mistake, it’s gone. Either someone else has it, or it went to a non-active address.
In one type of scam called address poisoning, bad actors send a small amount of crypto from an address that looks similar to one you’ve transacted with previously. Blockchain explorers make all this information available, and a vanity address creator makes it possible to create a similar wallet address. The hope is that you’ll inadvertently send crypto to the scam address, thinking it’s the one you’ve used before, perhaps a friend’s wallet or another wallet address you control.
When sending crypto, check the entire address, character by character, to ensure it matches the intended address.
Security Best Practices When Making Transactions
Bitcoin, the first cryptocurrency to reach a broad market, was invented to give us a way to transact in a currency controlled by the market rather than by governments. However, that also comes with some responsibility to protect ourselves. Following a few simple crypto security best practices can help you eliminate much of the risk when making crypto transactions.
Secure Internet Connection (Private Networks)
Man-in-the-middle attacks are common in places where people use public WiFi. In this situation, someone shares an internet connection, giving their shared connection an innocent-sounding name, perhaps named after the coffee shop or shopping center they are targeting. People then connect to the free network, unknowingly allowing the hacker to monitor their traffic. As you can imagine, crypto traffic is particularly interesting. The bits of data collected about your online activities can be used to identify you and make you a target.
Whenever possible, use a trusted private network for your crypto transactions. You can also consider using a quality virtual private network (VPN) provider. A VPN creates an encrypted tunnel, preventing internet service providers or man-in-the-middle attackers from seeing your network traffic.
Verify Transaction Details
Double-check all the details before making a crypto transaction. Some crypto wallets show a USD value for transactions, this can be helpful in preventing sending 10 ETH when you meant to send $10 worth of ETH.
Also, verify that you’re using the correct network. Crypto sent over the incorrect blockchain network is lost forever. Think of it as a 404 error on a website; address-not-found errors are costly in crypto.
After you make your transaction, you can view the transaction using a crypto wallet or a blockchain explorer. For example, etherscan.io tracks Ethereum transactions.
A blockchain explorer can’t prevent address or amount errors, but these tools can be handy if you need proof of a transaction or want to research wallet activity.
Avoid Publicizing Your Transactions
Public blockchains like Bitcoin and Ethereum make transactions visible to all. However, the transaction isn’t linked to your real identity — unless you make that information available. A few careless clues can put someone on your trail. Avoid discussing your crypto transactions with others. If someone can link your crypto address to your identity, you can become a target for phishing or even physical risks.
Biggest Crypto Security Issues
Actionable crypto security risks range from safeguarding your crypto wallet to dodging scams. However, it’s also crucial to exercise caution in who you share information with. Someone who knows you use crypto, possibly with large balances, could become a risk. Let’s consider some of the main issues surrounding cryptocurrency and security.
- Wallet security: Protect your private keys and seed phrases. If your hardware or software wallet supports hidden wallets, consider using them. This allows you to hide larger balances while making smaller balances available.
- Exchange security: Exchanges are a risk in that they often hold your personal information, including your name, address, login credentials, and perhaps even your social security number and driver’s license or passport. They’re also a target for hackers, dishonest insiders, or mismanagement that can end in the exchange’s collapse. Many traders only use exchanges for trades, moving their crypto off the exchange when the trade is complete.
- Phishing scams: Phishing exploits aren’t unique to crypto. However, the practice is prevalent in the crypto world. Double-check URLs before clicking links and delete any suspicious emails, texts, or messages.
- Smart contracts: Smart contracts are computer programs that run on the blockchain. These apps make decentralized finance and web3 games possible, but can also be the target of exploits. Research the audit history for crypto apps before connecting your wallet or interacting with smart contracts.
- Token contracts: While not a concern for mainstream cryptos like BTC and ETH, tokens themselves can be a risk. Some tokens prevent sales or impose a transaction tax that effectively steals crypto from traders. This is ost often seen with meme coins on decentralized exchanges.
- Doxing: Crypto allows you to transact using a pseudonymous wallet address. However, be careful not to let your wallet address become associated with your real identity. Many crypto wallets allow you to generate a new wallet address for sending crypto, protecting the privacy of your other wallet addresses.
Which Cryptocurrency is Most Secure?
Bitcoin is generally considered to be the most secure cryptocurrency. Bitcoin’s network uses proof of work to secure the transactions so they can’t be altered. Miners around the world generate hashes to find the next block to hold transactions. The sheer size of the network, combined with its growing hash rate, makes Bitcoin transactions extremely secure.
In 2019, BSV, a fork of Bitcoin, suffered a 51% attack, reorganizing up to 100 blocks of transactions. Smaller proof-of-work protocols are more vulnerable to brute-force attacks of this nature.
However, the most secure cryptocurrency could still be at risk if users don’t take steps to protect themselves in crypto transactions and crypto-related interactions.
The Role of Regulation in Crypto Security
Clear crypto regulation could help bolster crypto security, making the space safer for investors and more difficult for the industry’s shady characters. Major crypto exchanges like Coinbase already enforce identity verification to comply with Anti-Money Laundering (AML) and Know Your Customer (KYC) requirements.
However, governments are also concerned about tax evasion, which may play a role in the increased legal challenges to the crypto industry. Expect to see global partnerships such as the Crypto-Asset Reporting Framework (CARF), designed to share tax information.
For example, Switzerland’s AML regulations require identity verification for crypto transactions exceeding 1,000 Swiss Francs. Canada has proposed rules to govern crypto storage by custodians and investment funds, requiring offline cold storage and limiting eligible assets. Both strategies aim to enhance digital currency security for investors or the space as a whole.
Anti-Money Laundering (AML) Measures
Anti-money laundering rules follow a similar template in many jurisdictions worldwide. Crypto’s pseudonymous wallet addresses can make it attractive to criminals, making the space riskier for new investors. AML rules also dovetail with Counter-terrorism financing (CTF) initiatives, both seeking to eliminate crypto’s illicit use cases while creating a safer environment for investors.
KYC Verification
Financial institutions worldwide must also follow KYC requirements according to their jurisdiction. KYC is a requirement for banks and financial institutions, including brokerages in many countries, including the US. Crypto exchanges operating in these jurisdictions are required to collect identity verification documents, such as a passport or driver’s license. Still, there are several no-KYC crypto wallets and no-KYC crypto exchanges operating in the space.
Why Cybersecurity in Crypto is Challenging
Outside of exchanges and transactions involving intermediaries like brokers, crypto remains a nearly anonymous trade. While privacy advocates prefer this structure, it also creates challenges in crypto-related cybersecurity.
Difficulty in Identifying Involved Parties
Crypto users transact using a wallet address. In the event of a rug-pull scam, it’s possible to see where the crypto went, but it’s not as easy to identify who pulled off the scam. Following the crypto from wallet to wallet could lead to dead ends as the assets change hands again and again. Crypto mixers also make it possible to ‘launder’ the crypto to different wallets, making tracing the crypto nearly impossible.
Vulnerability to Hacking
Most crypto hacks are better described as exploits, meaning someone found a way to make a smart contract behave in an unexpected way, and it paid off like a winning slot machine. Hacks are possible, however, particularly with exchanges where massive amounts of crypto are stored. Between 2011 and 2014, 647,000 bitcoins were stolen from the Mt. Gox exchange, the largest Bitcoin exchange in the world at the time.
In both cases, crypto brings some security vulnerabilities that are not seen in traditional finance.
Prevalence of Bad Actors
Criminals and bad actors find a home in crypto markets. For example, at any given time, dozens of rug-pull scams are happening on decentralized exchanges. Investors buy into a hot new token, only to find there’s no way to sell and take a profit. The money is gone just that fast.
These types of scams aren’t easy to prosecute because the perpetrators are using wallet addresses rather than their real identities. As a result, most scams become learning opportunities for buyers, who hopefully can spot the warning signs next time.
Conclusion
Because crypto is largely unregulated, cryptocurrency safety becomes the responsibility of users. When transaction on exchanges, choose your exchange carefully and consider moving your crypto off the exchange when you’re done trading. For wallet transactions, remember — never to share your private keys. Also, verify transaction details before sending crypto to another wallet. You can bolster your security further by using a hardware wallet to protect your crypto from online threats.
FAQs
How secure is cryptocurrency?
Cryptocurrencies and crypto wallets are typically very secure. However, in situations where users lose their crypto, they may have shared their private keys or fallen victim to a phishing scam.
What is the biggest security risk in crypto?
The largest risks security risks in crypto center on exchanges, which often hold personal information as well as crypto assets for users, and crypto wallets, which can be used in insecure ways, possibly leading to a loss.
Are crypto wallets secure?
Most crypto wallets are secure, although some software wallets have been exploited in the past. In many cases where crypto users lose crypto from their wallet, the user may have shared the private key or seed phrase without understanding the risks.
Are crypto exchanges safe to use?
With an estimated 600+ crypto exchanges worldwide, safety becomes a relative term. Well-established exchanges like Coinbase and Kraken are considered to be safer choices. Choose your crypto exchange carefully.
References
- The Ethereum Blockchain Explorer (etherscan.io)
- BSV Suffers 51% Attack: Report (yahoo.com)
- Switzerland Sticks to Tougher ID Checks for Crypto to Cash Transactions (yahoo.com)
- Canadian securities regulators seek feedback on rules for public investment funds holding crypto assets (securites-administrators.ca)
- Russian Nationals Charged With Hacking One Cryptocurrency Exchange and Illicitly Operating Another (justice.gov)
- How to Recognize and Avoid Phishing Scams (ftc.gov)







 Michael Graw
Michael Graw 
 Goran Radanovic
Goran Radanovic 
 Patrick Jennings
Patrick Jennings