ESET And Dutch Police Uncover Ebury Botnet’s Crypto Theft Operation

Slovakian cybersecurity firm ESET and the Dutch police uncovered a major crypto theft linked to the notorious Ebury botnet last week. The botnet has compromised over 400,000 servers in the past 15 years, making it a major threat to the sector.
ESET explained in a May 14 report that the Ebury botnet incident was first uncovered during a 2021 investigation by the Dutch National High Tech Crime Unit (NHTCU).
Ebury Botnet Operators Used AitM Attack to Steal Funds
The operatives found that the cybercriminals had been involved in a series of crypto thefts, specifically targeting Ethereum and Bitcoin nodes. According to the Dutch police, Botnet operators steal assets from unsuspecting users’ wallets when they enter their credentials on the infected servers.
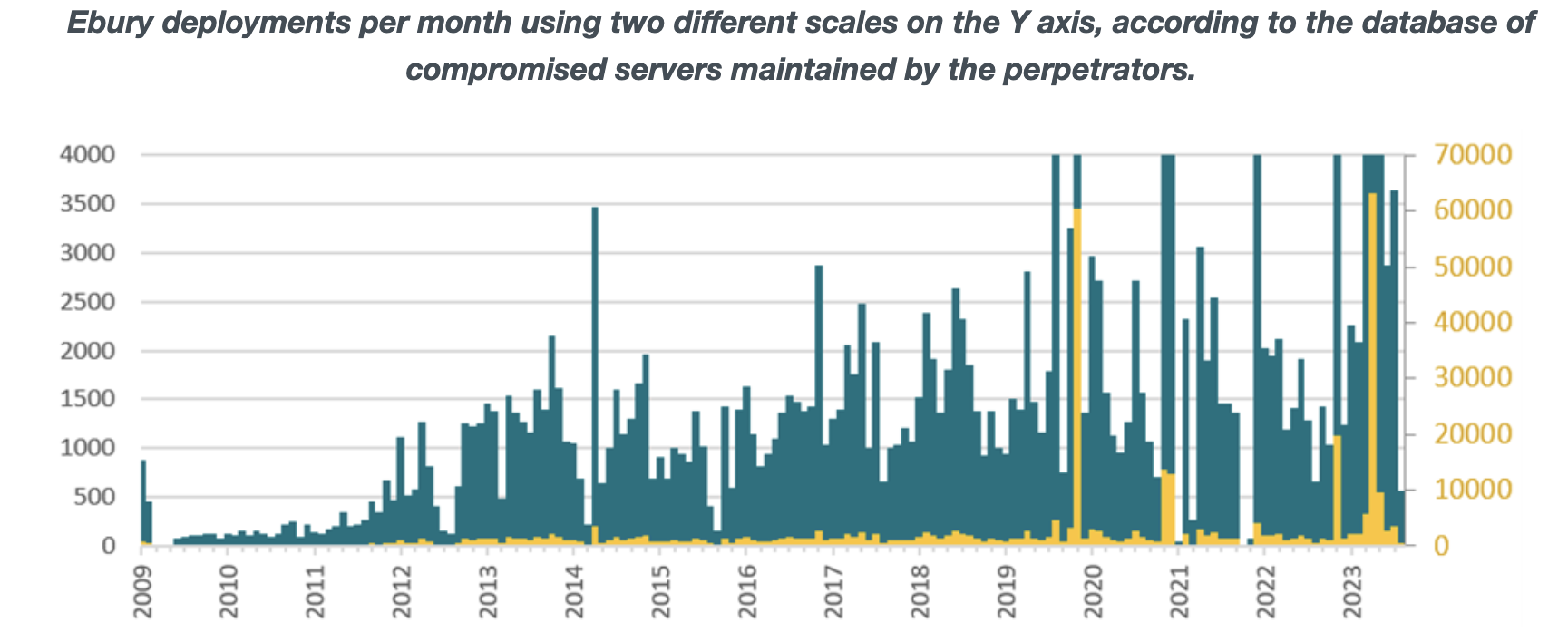
The Ebury botnet, active since at least 2009, is used to deploy additional malware, monetize the botnet (such as modules for web traffic redirection), proxy traffic for spam, perform adversary-in-the-middle (AitM) attacks, and host supporting malicious infrastructure.
AitM attacks involve intercepting and potentially altering the communication between two parties without their knowledge.
Between February 2022 and May 2023, the Ebury botnet compromised over 200 AitM attack targets across 75 networks in 34 countries. It stole cryptos, credentials, and credit card details, accumulating large sums of money over time.
The access enables them to steal funds directly from these wallets or use compromised systems to mine cryptocurrencies, siphoning off resources from unwitting victims. The botnet’s ability to stay undetected for long periods allows it to continue its operations, accumulating large amounts of cryptocurrency over time.
Crypto Theft on the Rise
The Ebury botnet’s ability to compromise many servers has created the go-to malware needed to facilitate large-scale cryptocurrency theft, which is already rapidly increasing.
Recall that PeckShield’s data shows that $336.8 million of crypto funds were stolen in the first quarter (Q1) of 2024. The Certik Hac3d Report also revealed that Q1 2024 recorded substantial losses, exceeding $500 million due to cryptocurrency theft, however. This figure marks a 54% increase compared to the same period in 2023, which saw losses of about $326 million.
Certik’s report highlighted that January 2024 was particularly severe, with $193 million stolen across 78 incidents. Private key compromises were especially notable, resulting in the loss of $239 million across just 26 incidents.
These breaches, targeting the unique keys that individuals use to access their cryptocurrency holdings, accounted for nearly half of all financial losses despite making up only 11.7% of all reported security breaches.








