Malicious Groups Collated Leaked Crypto Trader Data – BitMEX
After major cryptocurrency exchange BitMEX accidentally leaked users’ emails last week, they’ve noticed unidentified groups who tried collecting users’ email addresses with the intent to compromise them.

“As it became clear that several groups were working to collate BitMEX email addresses in order to attempt to compromise them, BitMEX engineers forced a password reset for all users with balances and without Two-Factor devices,” the company said in a blog post by Vivien Khoo, Deputy Chief Operating Officer, today. She did not provide any further details about the groups and damage they might have caused.
As reported, on November 1st, the exchange sent out a mass email about an update to their indices, but failed to ensure that the recipients’ email were hidden, instead leaving all of the emails in plain sight for anybody to see, which is a major security risk. At the time, they’ve acknowledged the breach and attributed it to a software error they claimed to have identified and fixed.
Today the company stated that their support team is contacting all affected users to help them protect their accounts and reset their passwords, advising them to enable Two-Factor Authentication (2FA) for all their accounts.
The exchange claims to have identified criteria that could point to a compromise, so they’ve cancelled requests from certain types of accounts, specifically those that:
- did not have two-factor authentication;
- were withdrawing to a previously unseen Bitcoin address;
- were submitted with previously unseen new IP address;
- were made after the email address disclosure had occurred.
As to what exactly led to this breach, the post claims that the exchange sends mass emails only when necessary, that one wasn’t sent since 2017, and acknowledge that, in this incident, many BitMEX user email addresses, “including a large number of inactive addresses, were disclosed to other users in small batches,” repeating that no other information was disclosed and no core systems were at risks. They further state that:
- as some mail servers are triggered by large emails, BitMEX built an in-house system to send emails to all of its users when its necessary to send a mass emails to all customers;
- as they saw that it would take up 10 hours to complete the email sending to all users, and wanting to deliver the information sooner, the exchange rewrote the tool to send single SendGrid API calls in batches of 1,000 addresses;
- as they haven’t allowed enough time to check this change, the API call created a “To:” field, leaking customer email addresses;
- the sending was stopped when the mistake was noticed;
- processes, not engineers, are to blame for these failures;
- the processes will be revamped so that all changes go through a strict review.
Most BitMEX users were affected by this action:
- those who were included among the multiple addresses in the “to” filed were affected;
- those who were the only ones in the “to” field were not affected;
- even if a user did not get this index update email, they could’ve been affected, as some emails which were sent hadn’t been delivered before certain hosts encountered problems to deliver them once users started marking BitMEX’s emails as spam in an attempt to protect themselves, meaning that these users’ addresses may have been included in an email delivered to somebody else.
Meanwhile, Vivien Khoo also claims that, unrelated to the breach, the BitMEX Twitter account was hacked, and that it “was back under BitMEX control within 6 minutes and re-secured, and the event is under security review.”
In the meantime, reacting to this blog post by the exchange, users asked for compensation and even suggested taking legal action against BitMEX. And while some were explaining how to protect one’s account on BitMEX, others claim to have left the exchange altogether.
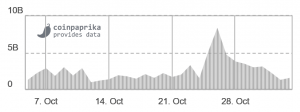
Trading volume on BitMEX: